Key takeaways
Payment security is (and should be) a top concern among businesses. Even with many regulatory standards in place, US businesses spent an average of $9.48 million in 2023 dealing with the effects of data breaches. An efficient payment security strategy costs little to set up and maintain in comparison and will help build consumer confidence in your brand.
What is payment security?
Payment security is a set of measures that is embedded in a business system and protects customers’ payment information from unauthorized access. These measures include the ability to detect breach attempts and flag fraudulent transactions before they happen. While online payment security is a huge concern, payment security for the entire business should be a priority. Every business that accepts credit cards as a form of payment should have security measures in place.
Why payment security is important
The average cost of data breaches globally hit an all-time high of $4.45 million in 2023; the United States led all regions with the highest data breach incidence for the 13th year in a row. Even consumers are sensitive about where they entrust their payment information, as over 60% are ready to walk away from retailers reported to have suffered from a data breach.
With a sound payment security strategy, businesses are equipped to minimize the risk of:
- Loss of revenue due to fraud (chargeback claims)
- Lawsuits and penalties from data breaches
- Loss of customers due to poor reputation
- Loss of the ability to accept credit card payments (blacklist from card networks)
Types of payment security
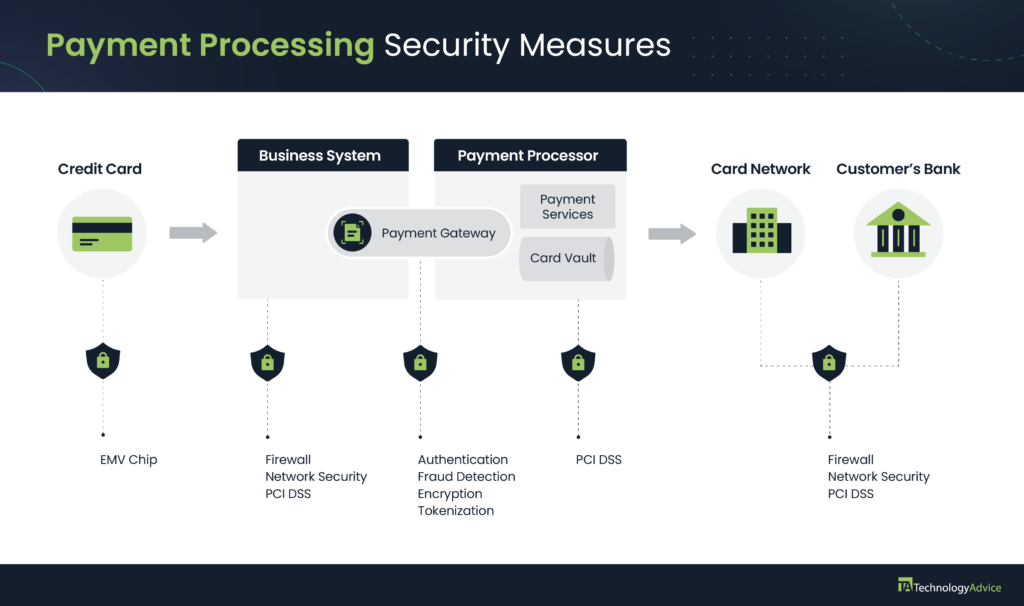
The best strategy for protecting payment information is a combination of security measures that match your business needs. The most common types of payment security include:
- EMV chip-equipped credit cards
- Firewall and network security
- Authentication
- Fraud detection
- Encryption
- Tokenization
- PCI DSS
EMV chip on physical credit card
EMV is named after Europay, Mastercard, and Visa, which created this security standard on physical credit cards. The EMV chip is the metallic chip embedded on a credit card (in place of the magnetic stripe on older card models) that stores cardholders’ information. Only specially designed card terminals can read the data in an EMV chip, which gives an extra layer of security against counterfeit credit cards being used to make payments. Instead of the customer’s credit card information, the merchant receives a one-time-use code to authenticate a transaction.
Most payment processors now support EMV chip-enabled card readers, and they do not cost extra to add to your credit card payment method.
Firewall and network security
Firewall and network security are used to protect an entire business system from data breaches, including unauthorized access to payment information. Security can be hardware- or software-based or both and controls data entering the computer network from company emails and any computer connected to the business system, not just from a payment gateway. Business software, such as POS systems, banks, and even card brands, all have advanced network security and firewalls in place to deter hackers and other external threats.
Network security can be as intricate as you want it to be, but the key is to assess and invest only based on what your business needs. For example, a small retail shop may not require much network segmentation (to keep payment data securely in one segment), but with many entry-level employees, role-based access control (RBAC) is a must.
Authentication
Whether through a storefront checkout counter, a website checkout page, a payment link, or a virtual terminal, users enter credit card information on a payment gateway. This makes the payment gateway a focal point of security when processing credit card transactions. Authentication is one such key security tool, particularly for payments done online. Its main function is to verify the identity of the user attempting to make a payment using the credit card.
Customers may know these authentication tools as:
- Card verification value (CVV): This is a three-digit or four-digit code found on credit (and debit) cards that users are prompted to enter on the payment gateway form to confirm the transaction.
- One-time password (OTP): The system sends a time-sensitive OTP to the cardholder’s verified mobile number and/or email and prompts the user to enter the OTP to complete the transaction.
- Biometric authentication: Some payment processors can be set up to use facial recognition, fingerprints, or iris scanning on a user’s mobile device to authenticate the customer’s identity.
- Security questions: To complete the transaction, the user is prompted to answer a security question designated by the cardholder at the time the account was activated.
- Physical tokens: A small device that serves as an authenticator. Users will be prompted to enter the number code displayed on the device into the payment form to validate the transaction.
- ID verification: For products or services exclusive to adults or certain locations, customers will be required to upload or scan a government-issued ID.
Payment processors allow businesses to set any one of the authentication tools above (single-factor authentication or SFA), and most payment processors allow for two-factor (2FA) and even multifactor authentication (MFA) settings.
Read more: Best virtual terminals
Fraud detection tools
Fraud detection tools are a requirement for online payment security. The payment processor should be equipped to recognize cues for potentially fraudulent transactions. These tools are designed via automated rules and machine-learning algorithms to detect IP proxies, identify unusual customer behavior based on their purchase history, and more.
Among the most common fraud detection tools are:
- Dynamic 3D Secure (3DS): 3DS is an additional verification tool that redirects customers to enter their password or a one-time code on their issuing bank’s site. This is often used for online credit card purchases of products or services where Strong Customer Authentication (SCA) is required.
- IP/Proxy detection: This allows the system to detect the user’s IP address and also whether they are using a proxy/VPN service to hide their actual IP address.
- Card testing protection: Some payment processors offer a payment gateway service that protects the business from a series of small-amount payments using stolen credit card information, which can result in increased disputes and chargeback claims. This is also often referred to as velocity checks.
- Machine-learning fraud detection: Machine-learning algorithms are designed to detect suspicious transactions by analyzing purchase history. The provider gives the business the ability to refine these settings from a fraud protection platform.
Most fraud detection dashboards also include reporting and analytics. It tracks which transactions are being blocked and the risk assessment of each attempted transaction based on set fraud detection rules. This provides businesses with timely information and allows them to evaluate the effectiveness of their payment security strategy, including acceptance rates, fraudulent chargebacks, and more.
The fastest way to set up fraud detection is to work with a payment processor, such as Stripe and PayPal, that also provides its own payment gateway to seamlessly integrate fraud detection tools into your payment security strategy.
Read more: Stripe vs PayPal comparison
Encryption
Encryption masks the customer’s financial information with advanced algorithms. The most common types are Secure Sockets Layer (SSL) and Transport Layer Security (TLS), which protect data transmitted between the customer’s browser and the business payment platform. Once data is encrypted on the payment gateway, the only way to unlock (decrypt) the information is to have a key.
- Symmetric encryption: The same algorithm is used to “lock” and “unlock” the data.
- Asymmetric encryption: A public or shared “key” is used to encrypt the data, while a private key is sent to payment processors, card networks, and banks to decrypt the information.
These encryption algorithms are effective with the help of regular assessment, key changes, and secure storage.
Tokenization
With tokenization, a secure system replaces the customer’s financial information with random, unique tokens to reference the transaction. This approach also makes the data useless to hackers; however, unlike encryptions, tokens do not have keys that can be used to convert it back into the original data. There are single-use (for individual transactions) and multi-use tokens (one token for each account, often used for businesses that accept recurring payments) that are stored in a centralized vault, which expire after the transaction is completed or account is closed.
Read more: Recurring payments.
Payment Card Industry Data Security Standard (PCI DSS)
The Payment Card Industry (PCI) Security Standards Council, commissioned by card networks, established a 12-point guideline for securing the use of credit card information. Every institution that handles customer financial information, businesses, payment processors, and payment gateways needs to be PCI-compliant.
Payment processors can help businesses with the technical requirements to achieve PCI compliance. However, businesses can also do their part by:
- Regularly conducting a risk assessment of your company’s network/payment processing infrastructure to discover potential vulnerabilities in your payment security strategy.
- Update your system and install security patches whenever they’re available.
- Train your staff on best practices and how to secure their access to the business computer network.
Read more: Guide to PCI compliance
Tip: Using the illustration above and the list of payment security types, start an initial evaluation of your current business and payment processing security.
Top payment security concerns in 2024
In 2023, phishing for identity credentials, API keys, tokens, session cookies, and one-time passwords (OTPs) is still a common theme, with malware still one of the most used hacker tools.
- Just this March, AT&T reported a data breach that affected 73 million current and former customers. Personal information such as social security numbers and account numbers were accessed with malware. In May, Ticketmaster lost 560 million customer records to hackers who leaked the data and offered it for sale online.
However, the landscape of cyber threats in 2023 also showed a clear shift from using hands-off tools like malware to a more ‘interactive intrusion” approach. This strategy mimics user behavior, making it difficult to differentiate from a cyberattack like ransomware.
- Dell experienced a data breach just this May, where the hacker managed to set up partner accounts within Dell’s company portal. Once the accounts were authorized, the hacker sent 50 million requests to Dell as a brute force attack, resulting in 49 million compromised accounts.
Hackers are also actively exploring vendor-client relationships, which businesses may overlook when developing their payment security strategy. The complex nature of B2B transactions has the potential to create unique payment system vulnerabilities if left without regular risk assessment and updates.
- In February, also of this year, a ransomware attack on Bank of America was found to have targeted one of its service providers, McCamish Systems. This affected 57,000 customers, with data including social security numbers and credit card information.
Read more: High-risk merchant accounts
Payment security best practices
Consider the following best practices when establishing secure payment processing for your business.
Be PCI-compliant
In general, keeping your business PCI-compliant is the best way to ensure that your business is as secure as it can possibly be. The PCI DSS covers every measure that needs to be taken, from regularly assessing and testing your business network to making sure that every employee has been trained to protect themselves from potential threats and know their role in case of a breach.
This includes:
- Using a secure payment gateway
- Policies for storing credit card information
- Regular backing up of data
- Fixing vulnerabilities
- Keeping security software up to date
The standards are also regularly updated based on evolving threats, so businesses are always following the latest guidelines.
When in doubt, work with your payment services provider to discuss any questions you may have on payment security. It’s possible that they can refer you to a reputable business security company for proper consultation.
Create a tailored payment security strategy
There is no one-size-fits-all solution for payment security. Every business is unique—models, sales channels, and payment methods vary based on the industry, product, or service, and business size or volume. The strategy, therefore, is to choose a combination among the available options that will work best for how your business operates. This can be done by conducting an overall assessment and identifying the weakness in the security you have in place.
Include payment security in choosing a business partner
Beyond a customer’s access to your payment system, it’s also important to look at business partners and consider their business security while evaluating your own. Any computer outside your secure business network, when integrated, is an avenue for hackers to exploit and test for vulnerabilities. While small and new vendors operating from a residence may cost less, their unprotected system, accessed by anyone within the premises may be a great risk.
Choose a payment processor with a dispute management feature
The best payment processors can provide users with a dispute resolution platform. It helps streamline the process if users can respond and monitor chargeback claims within the merchant account. Having this data integrated with the payment processing service also provides valuable information when trying to analyze the effectiveness of your payment security strategy.
Consider customer experience
Customer experience should also be considered. For online transactions, too many transaction fields, rerouted payment pages, and multiple login requests will scare customers away and result in cart abandonment. At times, these can’t be helped, so make an effort to let customers know the reason behind the requested actions with a clearly marked explanation on your payment pages. Encourage two-factor authentication using their mobile number for security and let them know why this benefits them the most. Most likely, customers will appreciate that you took the time to show them that their sensitive information is secured on your website.
Read more: Ecommerce payment processing





